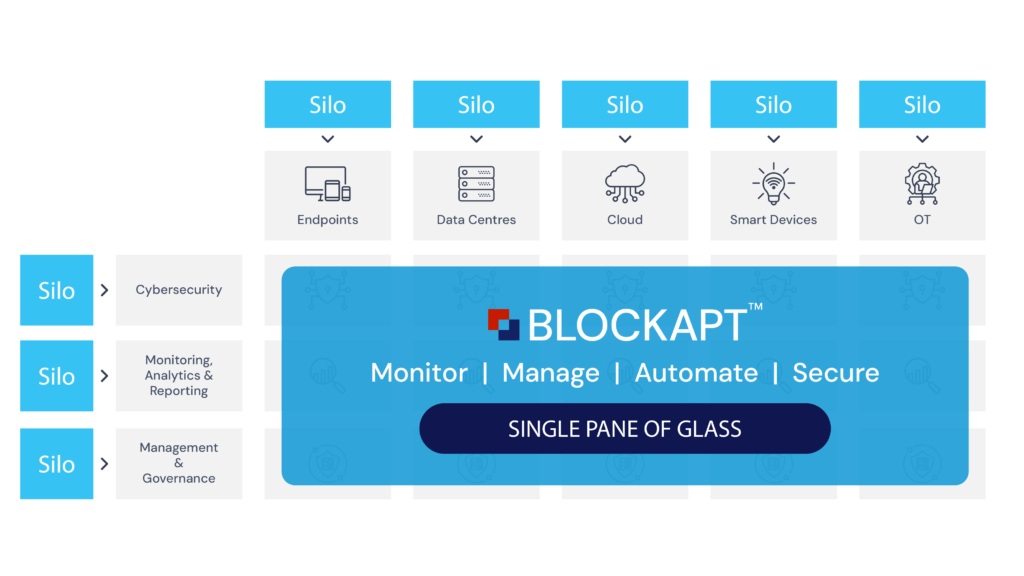
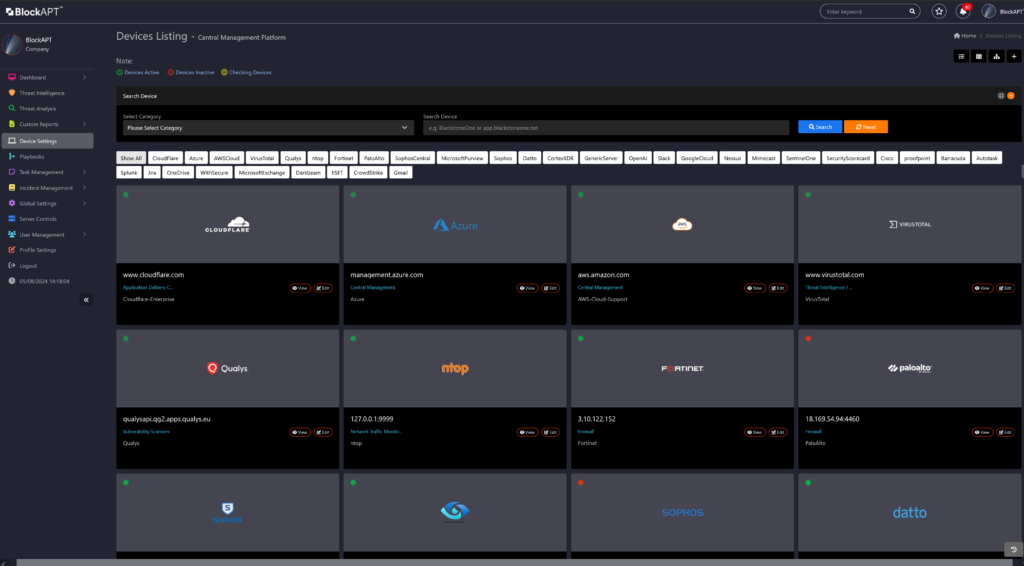
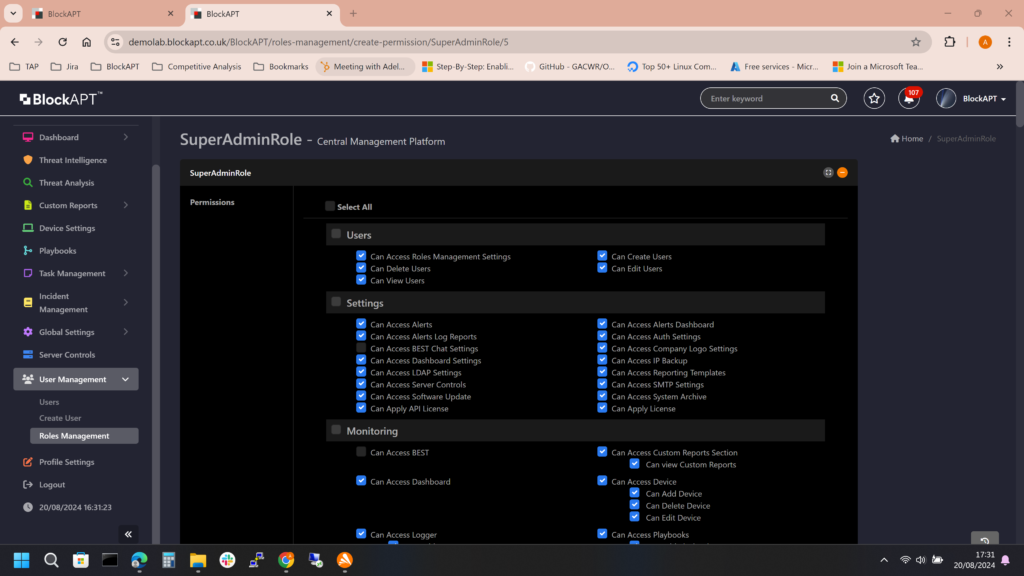
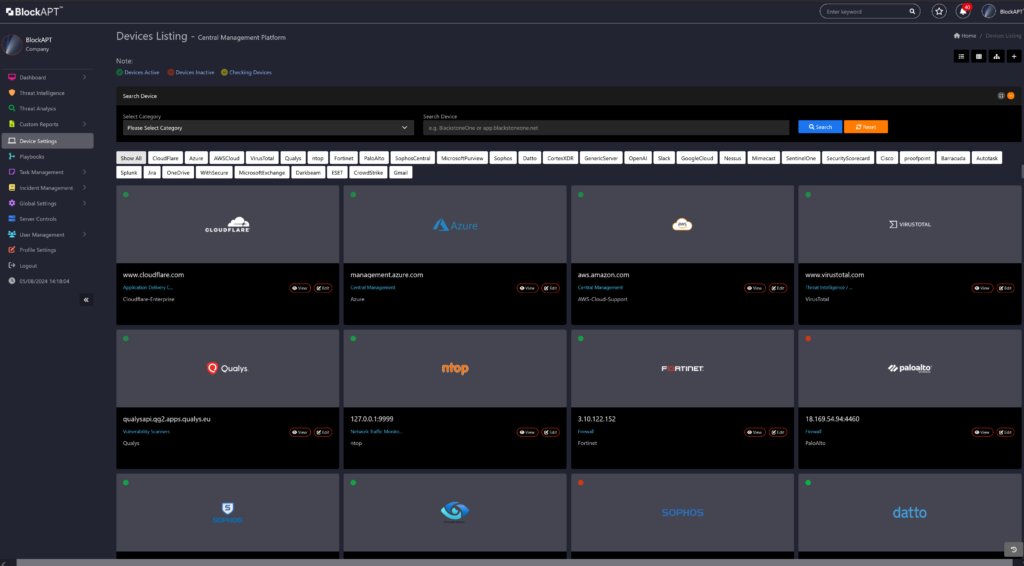
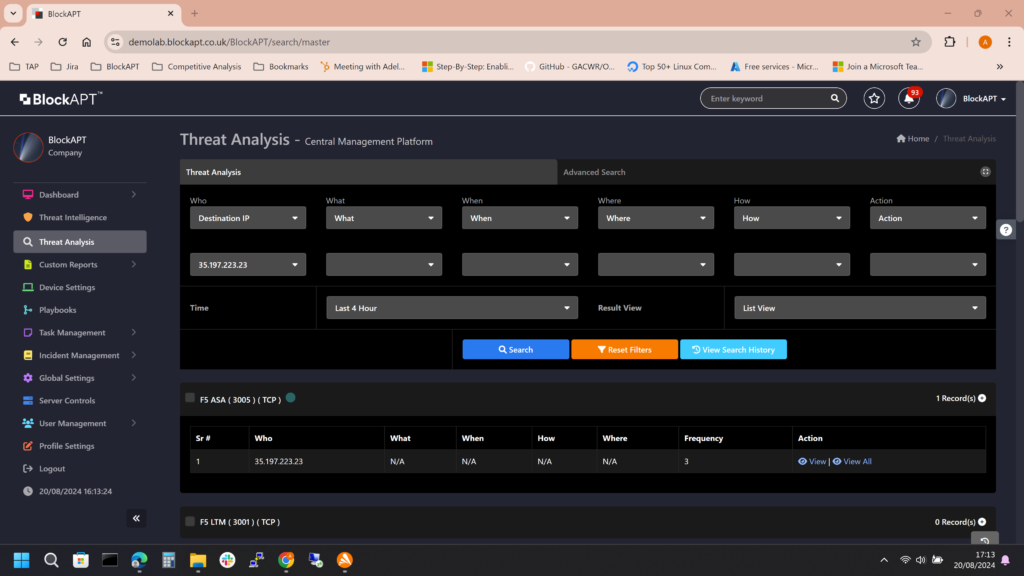
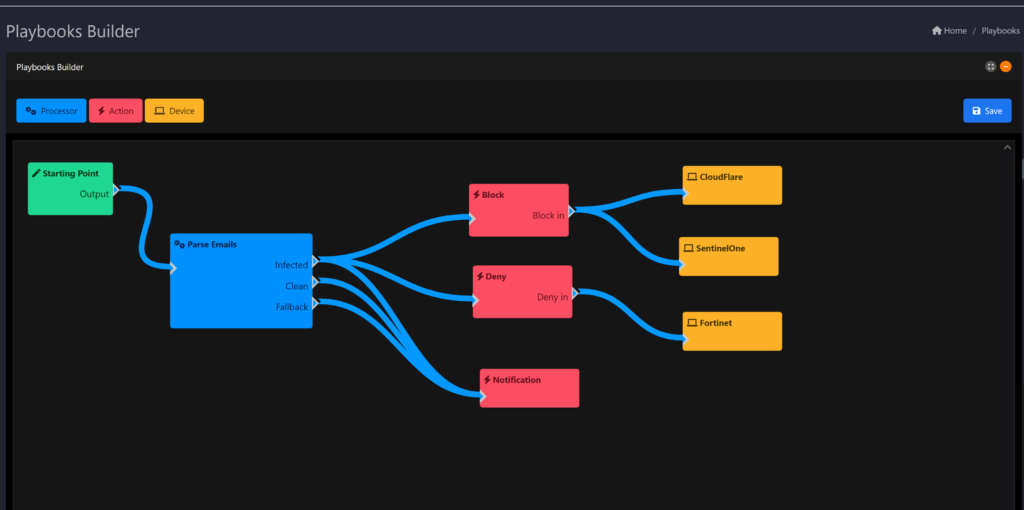
BlockAPT’s Control module enables organisations to seamlessly integrate, monitor, centralise management and natively control data against threats. Smarter orchestration to automate critical processes, streamline workflows, and accelerate incident response across infrastructures.
Vendor and sector agnostic, it optimises SecOps, reduces operational costs and enhances cyber resilience – all from a single pane of glass.
Why use BlockAPT Control?
Centralise management
- Unify apps, tools, and devices seamlessly to eliminate silos and gain total control.
Enhance malware defences
- Automatically analyse, contain, and remediate threats from one interface.
End alert fatigue
– Boost analyst efficiencies with prioritised, unified threat views.
Accelerate Threat Hunting
- Reduce MTTD and MTTR across teams and geographies.
Instant intelligence
- Transform raw data into actionable intelligence utilising real-time analytics and machine learning.
Workflow automation
– Customise playbooks to automate routine, mundane tasks
Maximise ROI
– Leverage economies of scale by optimising resources and scaling SecOps and NetOps efficiently.
Centralise management
- Unify apps, tools, and devices seamlessly to eliminate silos and gain total control.
Enhance malware defences
- Automatically analyse, contain, and remediate threats from one interface.
End alert fatigue
– Boost analyst efficiencies with prioritised, unified threat views.
Accelerate Threat Hunting
- Reduce MTTD and MTTR across teams and geographies.
Instant intelligence
- Transform raw data into actionable intelligence utilising real-time analytics and machine learning.
Workflow automation
– Customise playbooks to automate routine, mundane tasks
Maximise ROI
– Leverage economies of scale by optimising resources and scaling SecOps and NetOps efficiently.
What can you get from BlockAPT Control?
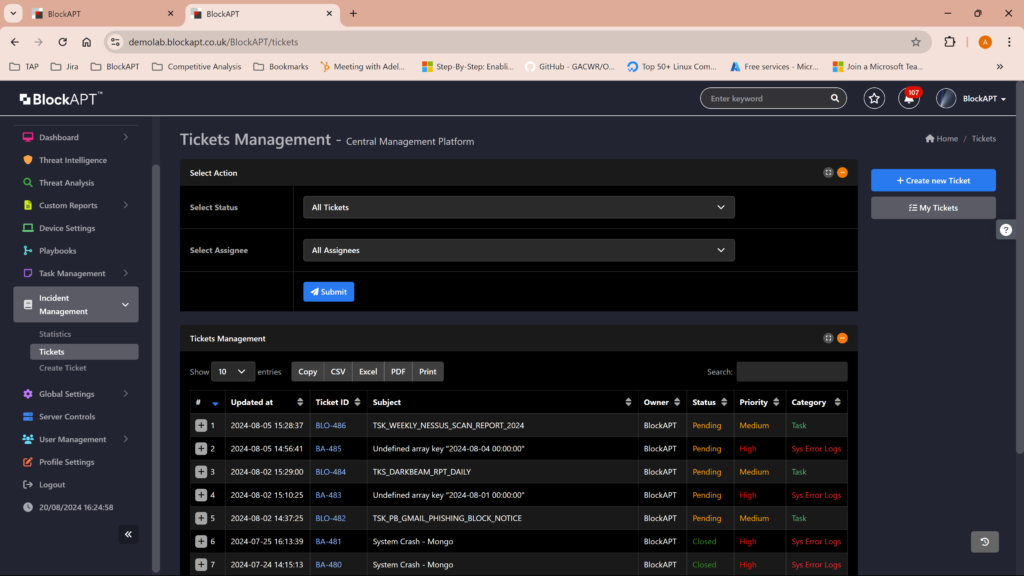
Orchestrated Incident Response:
- Customisable playbooks for automated response actions.
- Integration with existing security tools for coordinated defence.
- Case management for streamlined incident tracking and resolution.
Deep Insights & Intelligence:
- Transform raw data into actionable insights utilising advanced analytics.
- Visualise complex data at a glance across your entire infrastructure.
- Leverage customisable dashboards and an Executive Dashboard for management reporting.
Compliance & Audit:
- Simplify compliance processes and reporting for frameworks such as GDPR, NIS Regulations and FCA requirements.
- Leverage change control to identify key changes and track accountability to support audit trails.
- Leverage the centralised management capability to support your Cyber Essentials, Cyber Essentials Plus and ISO 27001 certification processes.
Pricing
Blockapt control includes:
control-small
-
250 x device licences included
-
3 x new integrations included
-
Support (Standard Support and Maintenance (9am-5pm GMT Monday-Friday, excluding public holidays)
-
1 year subscription
-
Additional device licenses, new integration requests and professional services available on request.
control-medium
-
500 x device licences included
-
3 x new integrations included
-
Support (Standard Support and Maintenance (9am-5pm GMT Monday-Friday, excluding public holidays)
-
1 year subscription
-
Additional device licenses, new integration requests and professional services available on request.
control-large
-
1000 x device licences included
-
3 x new integrations included
-
Support (Standard Support and Maintenance (9am-5pm GMT Monday-Friday, excluding public holidays)
-
1 year subscription
-
Additional device licenses, new integration requests and professional services available on request.
For BESPOKE solution requests, please reach out to our Sales team.
Use Cases

Attackers often use convincing emails that appear to be from a trusted source to trick users into providing sensitive information or downloading malware. Advanced detection against sophisticated social engineering protects teams from evolving email threats.