Increasing visibility is key for fighting the emerging threats.

We are witnessing an ever-evolving scenario in digital, but one that has at its base a world that is becoming increasingly interconnected, thus changing the risk posture of even items that previously did not foresee a networked scenario. In this context, cybersecurity has become a significant concern for individuals, businesses, and governments. Cyber threats, unfortunately, have evolved and intensified over the past few years, making it essential to take effective and innovative measures to protect our data, identities, and the systems that host them.

The advent of the COVID-19 pandemic has set the stage for significant changes in many areas, including cybersecurity. With the accelerated adoption of cloud computing, COVID-19 has redefined cyber scenarios and posed new challenges for protecting data and information systems. With the increased remote work and forced digitization of daily activities, organizations have faced new vulnerabilities and threats. In addition, cloud computing has emerged as an essential response to the need for connectivity, flexibility, and scalability during the pandemic. The cloud has provided new opportunities for work and collaboration, enabling organizations to operate effectively even in times of crisis. However, migrating to the cloud requires the right security measures to protect sensitive data. The cybersecurity landscape is constantly evolving, and the combination of the scenarios created post-COVID-19 and cloud computing combined with the ongoing digital transformation process requires the development of new strategies to protect our networks, data, and identities in an increasingly interconnected and digital world.
All these situations teach us how important it is to be agile and flexible. The complexity of threats has intensified, and the areas of vulnerability have expanded. These challenges have emerged because of the accelerating cloud transformation and the dissolution of traditional boundaries of enterprise networks and distributed workforce. As a result, there is growing interest in security strategies emphasizing security controls covering a wide range of resources, including multicloud ecosystems.

The adoption of multicloud and remote working has dramatically increased the complexity of cybersecurity. Most organizations today turn to different cloud providers offering service models such as IaaS, SaaS, and PaaS. In addition, individual applications often span multiple cloud service models provided by various providers. The fragmentation of technology ecosystems has further worsened with the growth of cloud computing and the decentralization of the workforce. Currently, employees are distributed everywhere, leading to increased demand for distributed technologies and the adoption of SaaS services.
The security needs emerging in this new situation are not answered by traditional architectures and strategies; a new approach is needed. This is where cybersecurity mesh (CSMA) comes in to minimize the need for a specific IT environment.
CSMA the Gartner definition.
The term “cybersecurity mesh” was coined by analyst firm Gartner, which called CSMA one of the key strategic technology trends in 2022. Gartner defines cybersecurity mesh architecture as a “common, broad, and unified approach that extends security beyond the enterprise perimeters.” According to Gartner, CSMA focuses on composability, scalability, and interoperability to create a collaborative ecosystem of security tools.
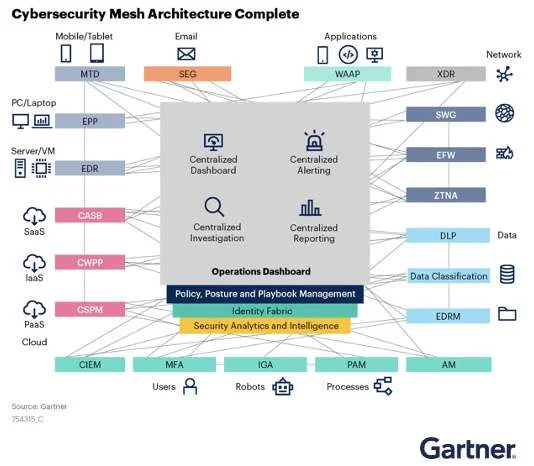
What is the Cybersecurity Mesh Architecture (CSMA)?
As mentioned, the Cybersecurity Mesh Architecture (CSMA) is a security architecture idea proposed by Gartner. CSMA’s distributed architectural approach aims to provide scalable, flexible, and reliable cybersecurity control. This architecture provides a fundamental base layer that facilitates a dynamic security environment, enabling different security services to operate synergistically. CSMA’s core approach focuses on security modularity, where each tool is carefully integrated into a larger framework. The CSMA presents a collaborative approach for distributed security services, thus providing increased power to achieve greater security cohesion with fewer resources. To achieve this goal, CSMA takes a unique path by configuring and managing four core layers for distinct security services.
Security analytics and intelligence:
The first level focuses primarily on the collection and analysis of security data provided by various security tools within a company’s security ecosystem.
Distributed identity fabric:
This layer prepares and provides the security framework with decentralized directory services that are fundamental to a zero-trust model. These include adaptive access, identity proofing, decentralized and user rights management.
Consolidated policy and posture management:
This layer aids in the configuration of individual security tools by translating a central policy into native configuration constructs. This allows for consistent and standardized security policies across security systems.
Consolidated dashboards:
Integrating disconnected security tools often requires switching between multiple dashboards, hindering operations. This layer provides an effective single-panel dashboard to view and manage an organization’s entire security ecosystem.

How to implement a Cybersecurity Mesh architecture?
Although Cybersecurity Mesh is a Gartner concept, specific steps can protect an organization’s critical access points and help create a more connected, tight-knit security infrastructure network. These steps include:
Interoperability should be a top priority when choosing security solutions for your cybersecurity infrastructure. Invest in creating an integrated framework of compatible security tools to achieve a more synergistic effect.
Choose tools that work as part of a larger framework rather than as independent silos. Priority should be given to vendors with an open policy framework that allows policy decisions to be made outside of the tool.
Provide resource access authorization only to authorized users, overseeing each request to detect malicious activity.
Select vendors with a proven track record of adapting to the latest security standards
latest and able to adapt readily to any new changes.
The transition from traditional VPN services to reliable and secure network access based on zero-trust technology, integrated with an access management tool.
Define KPIs and monitor them.
This is the only way to ensure the CSMA works well together and produces the expected results. The organization must identify the essential metrics to track and report, considering that there may be multiple KPIs to address. For example, a CISO may want to register specific KPIs at the board level to demonstrate that the CSMA strategy impacts business outcomes. At the same time, individual teams will need to measure separate KPIs to assess overall security posture and cyber resilience.
Final thoughts.
Cybersecurity Mesh is a new cyber defense strategy. As explained earlier, the Cyber Security Mesh Architecture (CSMA) includes four layers to configure and manage distinct security services: security analytics and intelligence, Distributed identity fabric, Consolidated policy and posture management, and Consolidated dashboards. Gartner predicts that by 2024, organizations adopting a cybersecurity mesh architecture will reduce the financial impact of individual security incidents by an average of 90 percent.